|
|
Keeping Secrets (Part 3)
 If you don't care that private details about your
finances, medical history, and sensitive personal
matters may become public knowledge, you can safely
ignore what I'm about to tell you. Likewise, if
you're 100% certain there's nothing on your
computer's hard drive you wouldn't mind seeing
printed on the front page of tomorrow's newspaper,
it's OK to save yourself a little reading time.
(There are some silly things over there in the right
column to amuse you instead.) However, if you would
like to know how I keep my private life private, how
I send and receive sensitive email messages with
absolute assurance they've never been intercepted or
altered, and how I make sure my laptop computer, if
stolen, has zero value to anyone but me, read on
brother. If you don't care that private details about your
finances, medical history, and sensitive personal
matters may become public knowledge, you can safely
ignore what I'm about to tell you. Likewise, if
you're 100% certain there's nothing on your
computer's hard drive you wouldn't mind seeing
printed on the front page of tomorrow's newspaper,
it's OK to save yourself a little reading time.
(There are some silly things over there in the right
column to amuse you instead.) However, if you would
like to know how I keep my private life private, how
I send and receive sensitive email messages with
absolute assurance they've never been intercepted or
altered, and how I make sure my laptop computer, if
stolen, has zero value to anyone but me, read on
brother.
I can make those bold statements because I know about PGP. And, in just a few minutes, you will too. This is installment number three in the "Keeping Secrets" article series. Here are links for Part One and Part Two. If you've been following along, you already know a little bit about the background of encryption (Cesar's cipher and the Ovaltine secret decoder ring), "old school" cryptography (the airport courier with cuffed briefcase containing symmetric lock/unlock codes or codebooks), and lastly, the idea behind public key cryptography (PKC). As a quick reminder, PKC involves matched sets of keys: a private key that you keep very, very secret, and a public key that the world can see. You use your private key to lock (encrypt) and unlock (decrypt) secret messages. But you show your public key to everyone. They can use it to prepare a message only you can read. That's the beauty of PKC: no need to ever exchange "secret" codes with anyone. More Than Pretty Good
If I've made my case, and convinced you that it's time to get serious about securing your communications and private information, what's next? I'll give you the bad news first. You'll need to spend a little money. $83 dollars to be exact. That's how much it'll cost for a one-year single-user license of PGP Desktop Professional (after a 30-day free trial). PGP Desktop automates all the tough parts of dealing with this technology. It does a lot more, but here are the 3 main benefits from my perspective:
Training Wheels
PrivateMail adds a simple toolbar which gives you control over the security features of your email. There are 3 versions: Free, Pro, and Enterprise. Like PGP Desktop, PrivateMail also automates key generation and interchange. How to Trade Secret Messages with Victor
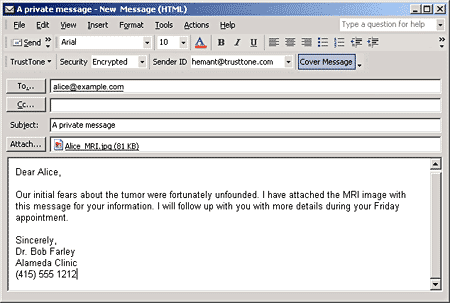
Urbach -----BEGIN PGP PUBLIC KEY
BLOCK----- You could just copy and paste that into your copy of PGP Desktop, but there's an easier way. Since I've also published it to the PGP Global Directory, a massive "Key Server" that functions like a global white pages for PGP keys, you can look me up (or find other folks you'd like to communicate with). Don't let the ugliness of that key block up there deter you from getting started with PGP. I included it more to show you what a public key looks like than anything else. Believe me, the software deals with all the hard stuff. It automates key exchanges, the encryption/decryption, and all the other techie stuff. You just need a general idea of what to do, which I hope this article has provided. There's more to the story though. Next month I'll show you how to make sure the document you just received as an email attachment is really from whom you think, and how to tell if anybody else has altered it. Stay tuned! |

 The
strategies I'm going to show you are perfectly
legal. You as a citizen have every right to maintain
the privacy of your documents and communications.
The
strategies I'm going to show you are perfectly
legal. You as a citizen have every right to maintain
the privacy of your documents and communications. Baby
Steps
Baby
Steps